Clear junk information 7 is your complete information to a cleaner, quicker laptop. We’ll delve into the world of undesirable information, displaying you how you can establish, take away, and forestall them from piling up. Get able to reclaim precious cupboard space and enhance your system’s efficiency!
This information explores varied sorts of junk information, from short-term information and cache knowledge to log information and installer remnants. We’ll cowl how these information accumulate, their potential detrimental impacts, and sensible strategies for eradicating them safely. Plus, we’ll share proactive methods to maintain your system operating easily in the long run.
Understanding “Clear Junk Recordsdata 7”
“Clear Junk Recordsdata 7” refers to a technique of eradicating pointless information out of your laptop. These information, usually referred to as “junk information,” can accumulate over time, probably slowing down your system and creating cupboard space points. Understanding what junk information are and the way they affect your laptop is essential for sustaining optimum efficiency.Junk information are primarily any file that is not actively wanted by your working system or put in functions.
They’ll embody short-term information, cache information, log information, and extra. These information are sometimes generated as byproducts of software program operation or system exercise, and whereas they may appear insignificant individually, their mixed impact will be vital.
Definition of Junk Recordsdata
Junk information, within the context of laptop programs, are undesirable or pointless knowledge that accumulate in your onerous drive or different storage gadgets. They’re usually short-term, cached, or log information that are not required for present operation. Their accumulation can result in efficiency points and wasted cupboard space.
Widespread Forms of Junk Recordsdata
A number of sorts of information can accumulate and be thought-about junk. They usually come up from varied sources and have completely different functions.
- Momentary Recordsdata: These are information created briefly by applications to carry knowledge throughout operations. They’re usually deleted robotically when this system finishes. Nonetheless, if this system crashes or is closed abruptly, these short-term information might stay. Examples embody information created throughout downloads, picture enhancing, or software program set up.
- Cache Recordsdata: These information retailer incessantly accessed knowledge to hurry up future retrieval. Internet browsers, for example, use caches to load webpages quicker. Whereas helpful, extreme cache information can bloat cupboard space and probably trigger conflicts.
- Log Recordsdata: These information report occasions and actions that happen in your system. They are often helpful for troubleshooting points, however massive log information may devour cupboard space.
- Downloaded Recordsdata: Whereas not all the time junk, downloaded information can develop into junk if they don’t seem to be wanted or deleted after use. These will be short-term or downloaded content material that’s not required.
- Utility-Particular Recordsdata: Numerous functions create short-term or cache information for his or her operation. These could be associated to file enhancing, software program updates, or different processes. These can range relying on the particular software.
Potential Detrimental Impacts of Junk Recordsdata
Accumulating junk information can considerably affect your laptop’s efficiency.
- Diminished System Efficiency: The sheer quantity of those information can decelerate system operations by consuming precious cupboard space and probably impacting system sources.
- Storage House Consumption: Over time, the buildup of junk information can occupy vital cupboard space, resulting in inadequate house for brand spanking new information and applications.
- System Instability: In some instances, junk information could cause system instability, resulting in crashes, errors, and different efficiency issues.
- Safety Dangers: Not often, however potential, are safety issues associated to improperly dealt with or saved short-term information. Improper cleanup might probably expose delicate info.
Examples of Software program Producing Junk Recordsdata
Numerous software program and functions can generate junk information.
- Internet Browsers: Browsers cache net pages and pictures to load them quicker. This generates cache information.
- Obtain Managers: These applications create short-term information throughout obtain processes.
- Workplace Suites: Microsoft Workplace, for instance, creates short-term information throughout doc enhancing.
- Multimedia Functions: Packages for video enhancing, picture manipulation, or audio recording can generate quite a few short-term information.
Comparability of Completely different Junk File Varieties
The next desk supplies a concise comparability of widespread junk file sorts.
| File Kind | Description | Potential Affect |
|---|---|---|
| Momentary Recordsdata | Created for short-term storage throughout operations. | House consumption, potential for instability if not deleted correctly. |
| Cache Recordsdata | Saved copies of incessantly accessed knowledge. | House consumption, potential for efficiency degradation if outdated or corrupted. |
| Log Recordsdata | File system occasions and actions. | House consumption, probably helpful for troubleshooting. |
Strategies for Figuring out Junk Recordsdata: Clear Junk Recordsdata 7
Discovering junk information could be a tedious job, however understanding their traits and areas makes the method considerably simpler. This part will information you thru varied strategies to pinpoint these undesirable information, serving to you filter out pointless litter.Figuring out junk information entails recognizing their widespread attributes, comparable to uncommon file extensions, sizes, and areas. Using file explorer options and command-line instruments will help you successfully goal and take away these information.
Widespread File Extensions Related to Junk Recordsdata
Numerous file extensions incessantly point out junk or short-term information. Realizing these extensions might help you shortly establish potential candidates. Widespread examples embody short-term information, cached knowledge, or installer remnants. This data streamlines the identification course of.
- .tmp, .log, .tmp, .swp, .bak, .chk, .previous, .crdownload, .half, .temp, .cache, .set up, .setup
Strategies for Discovering Junk Recordsdata Utilizing File Explorer
File Explorer affords intuitive methods to find junk information. These strategies leverage options like filtering by file sort, measurement, and modification date. This focused strategy helps you deal with probably problematic information.
- Filtering by File Kind: Search for information with the extensions listed above. You need to use the “View” tab in File Explorer to pick out the “Particulars” view, then kind by “Identify” to simply see the information with these extensions. Utilizing the search bar with particular extensions is one other environment friendly methodology.
- Filtering by Measurement: Junk information usually have unusually small or massive sizes. You possibly can filter by measurement to search out information exterior the standard vary on your information.
- Filtering by Modification Date: Momentary information and outdated backups usually have latest modification dates. Use the “Modified” column within the Particulars view to search out lately modified information.
- Filtering by Location: Junk information usually reside in particular folders or directories. Discover these directories rigorously to search out potential candidates.
Strategies for Discovering Junk Recordsdata Utilizing Command-Line Instruments
Command-line instruments supply superior methods to establish and find junk information. These instruments will be very useful for finding information with particular attributes.
- Utilizing the “discover” command (Home windows): The `discover` command in Home windows permits you to find information primarily based on varied standards, comparable to identify, measurement, and modification date. For instance, to search out all information with the extension “.tmp” within the “C:UsersYourUsername” listing, you should use a command like `discover “C:UsersYourUsername” /i “.tmp”`. The `/i` flag makes the search case-insensitive.
- Utilizing the “dir” command (Home windows): The `dir` command can be utilized to listing information in a listing. Mixed with filters, it may assist find information primarily based on particular attributes like measurement or date.
Categorizing Junk Recordsdata Based mostly on Nature and Objective
Categorizing junk information helps in understanding their objective and origin. This helps in making knowledgeable choices about which information to delete. A transparent understanding of what every file is permits you to prioritize your cleanup efforts.
- Momentary information: Recordsdata created for short-term storage throughout operations. These are sometimes marked with “.tmp” or related extensions.
- Downloaded information: Recordsdata downloaded however not but processed. They could have extensions like “.crdownload”.
- Backup information: Earlier variations of information or folders. They usually embody “.bak” or related extensions.
- Set up or configuration information: Leftover information from putting in software program or configuring programs.
Desk Exhibiting Places of Numerous Junk Recordsdata
This desk supplies a normal overview of areas the place several types of junk information could be discovered.
| File Kind | Typical Location |
|---|---|
| Momentary Recordsdata | %TEMP%, %TMP%, Utility-Particular Folders |
| Downloaded Recordsdata | Downloads Folder, Momentary Web Recordsdata |
| Backup Recordsdata | Backup Folders, File-Particular Backups |
| Set up Recordsdata | System folders, Program Recordsdata, Momentary Folders |
Instruments for Clearing Junk Recordsdata
Clearing junk information is not nearly tidying up; it is about optimizing your system’s efficiency. Pointless information can hog house, decelerate your laptop, and even create safety vulnerabilities. The fitting instruments can streamline this course of, saving you time and sources.
In style Software program Instruments
A number of devoted software program instruments are designed to establish and take away junk information. These usually transcend easy cleanup, providing superior options like analyzing completely different file sorts and offering detailed studies. Many supply intuitive interfaces, making them user-friendly, even for these unfamiliar with the intricacies of file administration. They incessantly scan your system for varied sorts of junk information, comparable to short-term information, cache information, and log information.
Clearing junk information 7 is an efficient technique to liberate house in your laptop. It will possibly actually assist velocity issues up, particularly in the event you’re coping with lots of previous information and knowledge. Should you’re on the lookout for particular methods to sort out this, trying out the wbery sources on wbery may offer you some useful insights, like completely different instruments and techniques.
In the end, clearing junk information 7 is an effective way to maintain your laptop operating easily.
- CCleaner: A well-liked and versatile software recognized for its capability to scrub up short-term information, registry entries, and browser cache. It is well-regarded for its user-friendly interface and complete cleanup choices. It is a highly effective software, however be cautious to solely choose particular cleansing choices you perceive.
- Clever Disk Cleaner: This software focuses on liberating up disk house by figuring out and eradicating pointless information. It supplies a transparent visible illustration of the house you may reclaim. This may be notably useful for customers who desire a easy technique to clear up disk house with out complicated configurations.
- BleachBit: This open-source software is superb for eradicating short-term information, logs, and cache knowledge throughout completely different functions. It’s particularly helpful for individuals who prioritize safety and desire a complete technique to take away previous knowledge.
Constructed-in Working System Instruments
Many working programs supply built-in instruments for managing and eradicating junk information. These instruments are sometimes built-in with the working system’s file administration options, making them simple to entry. Understanding the performance of those instruments can prevent the necessity to set up further software program.
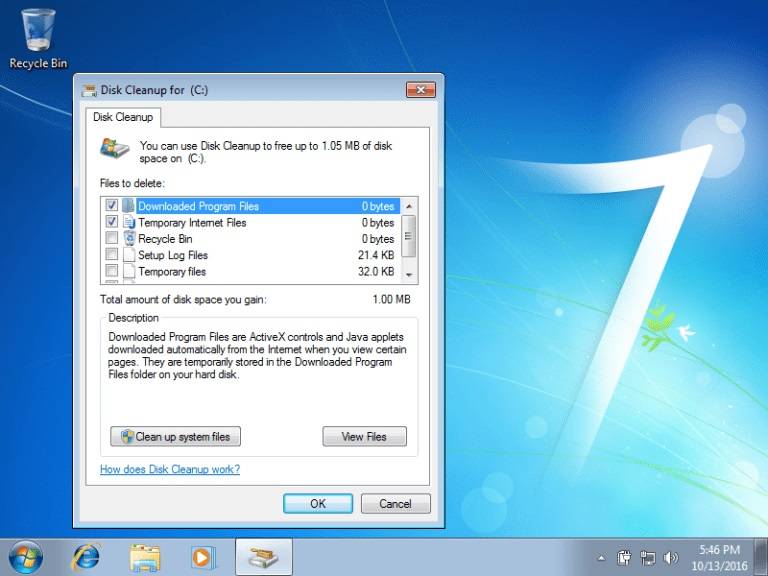
- Home windows Disk Cleanup: Home windows features a utility that may establish and take away varied short-term information and folders. It supplies a simple interface for choosing which information to delete. Utilizing this software will be notably helpful for clearing out previous short-term information.
- macOS Disk Utility: macOS affords Disk Utility, which incorporates choices to handle and optimize your onerous drive. It usually permits you to take away cached knowledge, and it may present particulars about your system’s storage utilization. This software is effective for sustaining macOS system efficiency.
Utilizing Third-Social gathering Software program
To make use of third-party software program, obtain and set up the applying. Comply with the on-screen directions for set up. As soon as put in, run the software program. The interface will range, however usually contains choices to scan your system for junk information. Choose the junk information you need to delete and click on the suitable button.
Utilizing Command-Line Utilities
Command-line utilities supply granular management over file administration. Utilizing instruments like `discover`, `rm`, or `trash` (relying on the working system) you may find and take away information matching particular standards. This strategy is usually obligatory for extra superior eventualities or conditions the place you want exact management over file deletion. Nonetheless, be extraordinarily cautious when utilizing command-line instruments, as errors may end up in everlasting knowledge loss.
| Device | Options | Professionals | Cons |
|---|---|---|---|
| CCleaner | Momentary information, registry entries, browser cache | Person-friendly, complete | Could be overkill for easy cleanup |
| Clever Disk Cleaner | Disk house optimization | Straightforward to make use of, visible illustration | Might not supply superior choices |
| BleachBit | Momentary information, logs, cache | Open-source, safe, complete | Steeper studying curve for rookies |
| Home windows Disk Cleanup | Momentary information, cached knowledge | Constructed-in, simple to make use of | Restricted performance |
| macOS Disk Utility | Exhausting drive administration, cached knowledge | Constructed-in, environment friendly | Restricted options in comparison with specialised instruments |
Procedures for Protected Junk File Removing

Eradicating junk information can considerably enhance your system’s efficiency, nevertheless it’s essential to do it safely. Improper removing can result in knowledge loss or system instability. This part Artikels the perfect practices for safely clearing junk information.Correctly figuring out and eradicating junk information is important for sustaining system well being and avoiding potential knowledge loss. Understanding the sorts of information that represent junk and the instruments for figuring out them is step one in a secure removing course of.
Significance of Knowledge Backup
Backing up necessary knowledge earlier than cleansing junk information is paramount. This safeguards towards unintended deletion of important information through the course of. Even with cautious choice, there’s all the time a slight danger of error. A backup supplies a security internet to revive any misplaced or corrupted information. Consider it like an insurance coverage coverage on your digital property.
Potential Dangers of Improper Junk File Removing
Improper junk file removing can have a number of hostile results. Unintentional deletion of obligatory system information can result in system instability, errors, and even crashes. Eradicating information related to operating functions may disrupt ongoing duties or trigger functions to malfunction. Corrupting information through the removing course of can render them unusable. A single incorrect transfer can create extra issues than it solves.
Protected Procedures for Junk File Removing
Protected junk file removing entails a scientific strategy to establish and delete pointless information whereas preserving important knowledge. Thorough planning and cautious execution are key to avoiding any potential injury. The next steps reveal a structured technique to clear junk information with out compromising the system.
Step-by-Step Information to Protected Junk File Removing
- Backup essential knowledge: Earlier than initiating any junk file removing course of, create a complete backup of all necessary information and folders. This ensures you’ve got a duplicate of your knowledge in case one thing goes incorrect.
- Establish junk information: Use dependable junk file identification instruments to pinpoint pointless information. Fastidiously look at the outcomes, verifying any questionable objects.
- Choose information for removing: Evaluation the recognized junk information. Affirm that the chosen information are actually pointless. Keep away from eradicating information related to operating applications or important system information.
- Take away junk information: Make use of the suitable instruments for secure removing of junk information. Many applications supply an possibility to maneuver information to the recycle bin or trash, offering a possibility to revive deleted information if obligatory.
- Confirm removing: After eradicating the information, verify if the junk information are literally deleted. Affirm that no necessary information had been inadvertently eliminated.
- Restart the system: Restarting the system after the removing course of ensures that any obligatory adjustments are mirrored and that the system operates optimally.
Protected Junk File Removing Course of Abstract
This desk Artikels the steps concerned in a secure junk file removing course of, emphasizing the significance of backups and verification.
| Step | Motion | Significance |
|---|---|---|
| 1 | Backup necessary knowledge | Protects towards unintended knowledge loss |
| 2 | Establish junk information | Ensures solely pointless information are focused |
| 3 | Choose information for removing | Avoids removing of important system information |
| 4 | Take away junk information | Makes use of applicable instruments for secure deletion |
| 5 | Confirm removing | Confirms profitable removing and no unintended loss |
| 6 | Restart the system | Ensures system stability and optimum efficiency |
Stopping Future Junk File Accumulation
Protecting your system clear is not nearly eradicating junk; it is about stopping it from piling up within the first place. Proactive measures can considerably cut back the quantity of litter your laptop accumulates over time, main to higher efficiency and a smoother person expertise. Understanding the basis causes of junk file creation and adjusting your software program and system settings are key to a wholesome, environment friendly system.Software program configurations play an important position within the quantity of junk information generated.
By understanding how completely different applications create short-term information, log information, and cache knowledge, you may alter settings to reduce this affect. Likewise, optimizing your system settings may assist forestall junk file accumulation. Common upkeep routines are important in making certain that the system stays wholesome and environment friendly, lowering the probability of pointless information accumulating.
Methods to Forestall Junk File Accumulation
Stopping junk information requires a multi-pronged strategy, specializing in each software program and system settings. Recurrently clearing short-term information and folders is a elementary step, stopping them from increase over time. This usually entails utilizing instruments offered by the working system or devoted third-party software program designed for this objective.
Configuring Software program to Decrease Junk File Technology
Completely different software program applications generate various quantities of junk information. Understanding how your applications deal with short-term knowledge, logs, and cache is essential. Many functions supply settings to regulate the scale and frequency of those information. Adjusting these settings can drastically cut back the amount of junk created.
- Browser Settings: Internet browsers retailer cached knowledge, cookies, and historical past information. Adjusting browser settings to clear cache and cookies often can forestall these information from accumulating. Trendy browsers usually supply choices for automated clearing of information at particular intervals or on exit.
- Obtain Managers: Obtain managers incessantly create short-term information through the obtain course of. Configure these instruments to robotically delete these short-term information as soon as the obtain is full. This may be executed throughout the obtain supervisor’s settings.
- Multimedia Gamers: Multimedia gamers usually create short-term information to deal with media playback. Evaluation settings inside these gamers to find out if short-term information will be robotically deleted. Recurrently deleting these short-term information after use will be helpful.
Optimizing System Settings to Cut back Junk File Creation
System settings usually affect how applications and functions handle short-term knowledge. Adjusting these settings can considerably cut back the quantity of junk generated. Take into account reviewing these settings to search out any alternatives for optimization.
Suggestions for Common System Upkeep to Forestall Junk File Buildup
Common system upkeep is essential for stopping junk file buildup. This contains often clearing short-term information, eradicating unused applications, and defragmenting the onerous drive (if obligatory). Sustaining a clear and environment friendly system will decrease the necessity for intensive junk file removing sooner or later.
- Common Disk Cleanup: Use the built-in disk cleanup utility to take away short-term information, older system information, and different pointless knowledge.
- Uninstall Unused Packages: Uninstalling applications you now not use eliminates related junk information and registry entries.
- Defragmenting Drives (Optionally available): Whereas much less essential on trendy programs, defragmentation might help keep drive efficiency and forestall fragmented information from contributing to junk.
Desk of Widespread Software program Settings Affecting Junk File Technology
This desk supplies a concise overview of widespread software program settings and their affect on junk file era.
| Software program Class | Setting | Affect on Junk Recordsdata |
|---|---|---|
| Internet Browsers | Cache Measurement | Bigger cache sizes result in extra cached information, probably rising junk. |
| Obtain Managers | Momentary File Deletion | Enabling automated short-term file deletion reduces junk file accumulation. |
| Multimedia Gamers | Cache Measurement/Momentary File Dealing with | Adjusting these settings can decrease short-term information generated throughout playback. |
| Working System | Disk Cleanup Utility | Common use can take away short-term information and different system junk. |
Troubleshooting Points Throughout Removing
Typically, even essentially the most cautious junk file removing can hit snags. This part delves into widespread issues and how you can repair them, making certain a easy and profitable cleanup. Realizing how you can deal with these points will prevent time and frustration.Figuring out the issue and understanding its trigger is essential to resolving junk file removing points. Usually, these issues stem from permission restrictions, corrupted information, or conflicts with different applications.
Widespread Removing Errors
Errors throughout junk file removing should not unusual. They’ll stem from quite a lot of causes, together with points with the removing instruments themselves or issues with the working system. Understanding the causes helps find the answer.
- Recordsdata marked as in use: Some information could be locked by one other program or course of. This prevents them from being deleted. Restarting this system that is utilizing the file, or restarting your laptop, usually resolves this.
- Permission errors: Your person account may not have the mandatory permissions to delete sure information. These errors will be resolved by adjusting permissions throughout the working system settings.
- Corrupted or inaccessible information: Broken or corrupted information can typically trigger removing instruments to fail or refuse to delete the information. Usually, these information should be recognized and both repaired or deleted in secure mode, relying on the character of the corruption.
- Software program conflicts: Sure applications may intrude with the junk file removing course of, inflicting errors or stopping the removing of particular information. Restarting the pc and checking for conflicting applications might help resolve this situation.
Resolving Points with Unremovable Recordsdata
Typically, a program will stubbornly refuse to delete particular information. Here is a step-by-step strategy to deal with these conditions.
- Establish the cussed file: Notice the file’s location and identify. This can enable you to pinpoint the issue and probably discover a resolution.
- Examine for conflicting applications: Search for any applications operating within the background that could be utilizing the file. Shut or restart these applications.
- Run the removing software in secure mode: Boot your laptop into secure mode. This atmosphere usually restricts operating applications, probably resolving points with conflicting software program. Re-attempt the file removing in secure mode.
- Modify file permissions: Use the working system’s file administration instruments to make sure your person account has applicable permissions to delete the file. Elevated privileges (administrator entry) could be required in some instances.
- Try handbook deletion: If the removing software fails, take into account manually deleting the file utilizing the working system’s file explorer. Nonetheless, be extraordinarily cautious when deleting information manually.
Addressing Permission Points
Permission points are widespread throughout junk file removing. Incorrect permissions can forestall the removing software from deleting particular information. Here is how you can resolve them.
- Establish the problematic file: Decide the file’s location and identify.
- Examine file permissions: Use the working system’s file properties to evaluation the permissions assigned to the file and folder.
- Modify permissions: Grant your person account the mandatory delete permissions to the file and its guardian folders. You may want to regulate permissions by way of the working system settings, or use an elevated command immediate.
- Run as administrator: Strive operating the removing software with administrator privileges. This usually grants the mandatory permissions to delete information.
Troubleshooting Desk
| Error | Answer |
|---|---|
| File in use | Restart program, restart laptop |
| Permission denied | Modify file permissions, run as administrator |
| Corrupted file | Establish and resolve the corruption, probably deleting in secure mode |
| Software program battle | Establish and shut conflicting applications, restart laptop |
Illustrative Examples of Junk Recordsdata
Junk information are primarily digital litter that your laptop accumulates over time. They’ll vary from short-term information created throughout software program use to remnants of uninstalled applications. Realizing what these information are and the place they reside is essential for efficient cleansing. Correct identification permits for focused removing, liberating up cupboard space and probably boosting system efficiency.Understanding the several types of junk information helps in distinguishing between important system information and people that may safely be eliminated.
This data permits you to strategy cleansing with a higher stage of confidence and accuracy.
Momentary Recordsdata, Clear junk information 7
Momentary information are created by applications as a holding place for knowledge throughout their execution. They usually include intermediate outcomes or cached knowledge. Their existence is normally short-term, lasting solely so long as this system utilizing them is operating. Nonetheless, if a program crashes or closes unexpectedly, these information may not be deleted.
- Traits: Momentary information usually have names that embody timestamps or distinctive identifiers, usually with extensions like “.tmp”, “.temp”, or “.dat”. They’re normally situated in short-term folders, comparable to %TEMP% or %TMP% on Home windows programs. They’ll additionally exist in application-specific directories.
- Examples: An internet browser may use short-term information to retailer photos or cached webpages for quicker loading. A phrase processor may use short-term information to save lots of intermediate variations of a doc throughout enhancing. A recreation may use short-term information to retailer high-scores or recreation progress knowledge.
Cache Recordsdata
Cache information retailer incessantly accessed knowledge to hurry up subsequent retrievals. They act as a reminiscence financial institution, lowering the necessity to retrieve info from slower sources, like onerous drives.
Clearing junk information 7 can actually assist your laptop run smoother, particularly in the event you’re coping with lots of short-term information. For instance, in the event you’re on the lookout for methods to liberate house and velocity up your system, trying out how you can clear junk information 7 is an efficient place to start out. Plus, in the event you’re curious about seeing what different persons are as much as on websites like amanda cerny onlyfans , you may discover some useful ideas there.
Clearing junk information 7 is all the time a good suggestion for optimizing your laptop’s efficiency regardless.
- Varieties: Browser caches retailer webpages, photos, and different sources for quicker loading. Utility caches retailer incessantly used knowledge particular to a program. System caches retailer incessantly used system knowledge for improved effectivity.
- Objective: The first objective of cache information is to boost efficiency by lowering the necessity for repeated entry to knowledge from slower sources. This considerably improves the responsiveness of functions and the general velocity of the system.
- Instance: An internet browser’s cache shops photos and web page components from incessantly visited web sites. This reduces the quantity of information that must be downloaded every time you revisit these websites.
Log Recordsdata
Log information report occasions that happen in your laptop. These occasions can embody errors, warnings, profitable operations, and different vital occurrences.
- Features: Log information are precious for troubleshooting points, monitoring system well being, and figuring out potential issues. They supply a chronological report of occasions that occurred on the system.
- Instance: An internet server may log each request made to its web site. These logs can be utilized to establish common pages, observe errors, and diagnose safety points. System log information present particulars about software program installations, updates, and system occasions.
Installer or Setup Recordsdata
Installer or setup information are short-term information created through the set up or setup of software program. They facilitate the set up course of, dealing with the switch and extraction of program information.
- Nature: These information usually have particular extensions, comparable to “.msi”, “.exe”, “.tmp”, or extensions associated to the set up program. They’re usually situated in short-term folders throughout set up. They’re usually eliminated as soon as the set up is full.
- Instance: When putting in a brand new software, short-term information are used to deal with the unpacking of information from the installer to the suitable listing.
System Recordsdata
System information are essential parts of your working system and different applications. They carry out important features to keep up system stability and performance.
- Features: System information are integral to the operation of your laptop. They supply the underlying construction and performance for all different applications and parts to work collectively. System information be sure that your laptop’s fundamental features work accurately, comparable to operating applications, managing information, and interacting with {hardware}.
- Instance: System information handle {hardware} drivers, management the working system’s core features, and help different applications within the system.
Final Level
In conclusion, understanding and successfully managing junk information is essential for a wholesome laptop. Clear junk information 7 has offered you with a sturdy framework for figuring out, eradicating, and stopping these information. By following the steps Artikeld, you may dramatically enhance your system’s efficiency and liberate precious cupboard space. Bear in mind to again up your necessary knowledge earlier than beginning any cleansing course of.
Completely satisfied computing!
Generally Requested Questions
What are some widespread sorts of junk information?
Momentary information, cache information, log information, installer remnants, and system information which are now not wanted are widespread examples. An in depth rationalization is included within the information.
What instruments can I exploit to take away junk information?
Each built-in working system instruments and devoted third-party software program can be utilized for junk file removing. The information will clarify completely different choices and their options.
How do I safely take away junk information?
All the time again up necessary knowledge earlier than cleansing. Use warning when eradicating information, particularly in the event you aren’t positive of their objective. The information contains secure removing procedures and step-by-step directions.
What occurs if I unintentionally delete a obligatory file?
The information covers potential errors and options to resolve points through the removing course of. It is necessary to watch out and observe the secure removing procedures.
