DNS iCloud bypass is a fancy matter involving understanding how DNS interprets domains to IP addresses and the way iCloud makes use of this method for authentication. This exploration delves into the strategies used to bypass DNS restrictions, the safety dangers concerned, and authorized and moral issues. It additionally examines different entry strategies, safety finest practices, and real-world examples.
This information offers a complete overview of DNS iCloud bypass, from elementary ideas to superior methods and potential dangers. It’s essential to grasp the intricacies of DNS and iCloud to navigate this house safely and successfully.
Understanding DNS and iCloud
So, you are trying to perceive how DNS and iCloud work collectively? Nice! This part dives into the basics of each methods and their interplay. Realizing how they join helps you admire the method behind accessing on-line companies like iCloud.DNS, or the Area Title System, is actually the telephone e book of the web. It interprets human-readable domains (like instance.com) into machine-readable IP addresses (like 192.168.1.1).
Icloud, however, is a collection of cloud companies offered by Apple. It shops your recordsdata, images, and different knowledge on-line. Let’s discover how these two methods join within the context of a typical consumer expertise.
Area Title System (DNS)
DNS acts as an middleman between you and the web. You kind a site title into your browser, and DNS finds the corresponding IP tackle. This course of occurs nearly instantaneously. DNS servers work in a hierarchical construction, making it very environment friendly. Consider it like a multi-level listing system.
DNS iCloud bypasses are a factor, however generally you want a particular device for sure duties. For instance, when you’re making an attempt to entry a particular mail server, like mailiholtx , you may want a distinct strategy than a common DNS bypass. Finally, the very best methodology for DNS iCloud bypass nonetheless relies on your state of affairs.
Whenever you kind a site title, your pc queries a neighborhood DNS server. If it would not have the reply, it queries higher-level servers till it finds the IP tackle.
iCloud Perform
iCloud offers on-line storage and synchronization in your Apple units. It enables you to entry your images, recordsdata, and different knowledge from anyplace with an web connection. Think about storing your paperwork in a digital cloud that is accessible out of your telephone, pill, or pc. iCloud makes use of varied applied sciences to make sure knowledge safety and reliability.
Interplay Between DNS and iCloud
Whenever you entry an iCloud service, your machine wants to seek out the iCloud servers. Your machine first makes use of DNS to resolve the area title related to iCloud (e.g., icloud.com). As soon as it will get the IP tackle, your machine can hook up with the suitable iCloud server and entry the requested knowledge. In essence, DNS is the preliminary step, offering the situation, whereas iCloud handles the precise service.
Desk: DNS and iCloud Ideas
| Idea | Description | Instance |
|---|---|---|
| Area Title System (DNS) | Interprets human-readable domains (like www.apple.com) into numerical IP addresses (like 17.172.216.164) that computer systems use to find sources on the web. | Typing “www.apple.com” in your browser triggers a DNS lookup to seek out the corresponding IP tackle. |
| iCloud | A collection of cloud companies offered by Apple, enabling on-line storage, synchronization, and entry to knowledge throughout varied Apple units. | Storing images, paperwork, and contacts on iCloud and accessing them out of your iPhone, iPad, or Mac. |
| Interplay | DNS resolves the iCloud area title (icloud.com) to its IP tackle, permitting your machine to connect with the iCloud servers and entry the requested knowledge. | Accessing your iCloud images. Your machine first queries DNS to seek out the iCloud server’s IP tackle; then, it makes use of that tackle to attach and retrieve your images. |
Exploring “Bypass” Methods
DNS bypass methods, typically used to avoid restrictions, can result in varied safety and authorized points. Understanding these strategies and their implications is essential for accountable web use. These strategies, whereas generally interesting for accessing blocked content material, typically include important dangers.
Frequent DNS Bypass Strategies
Totally different strategies exist to bypass DNS restrictions. Some contain modifying DNS settings in your machine, whereas others use third-party companies or software program. Understanding these strategies helps one consider their potential dangers.
- Utilizing different DNS servers: Many public DNS servers exist, comparable to Google Public DNS or Cloudflare DNS. Customers can configure their units to make use of these different servers as a substitute of their ISP’s default DNS, probably circumventing restrictions. This strategy could be helpful for accessing blocked web sites however carries inherent dangers.
- VPN companies: VPNs (Digital Personal Networks) masks your IP tackle, permitting you to look like related from a distinct location. This may successfully bypass DNS restrictions imposed by geolocation or censorship, however safety relies on the VPN supplier’s trustworthiness.
- Proxy servers: Proxy servers act as intermediaries between your machine and the web. They will ahead your requests by a distinct server, probably hiding your true location and bypassing restrictions. That is much like VPNs however typically much less safe.
- Specialised software program or instruments: Some specialised software program is designed to bypass DNS restrictions. These instruments could be respectable or malicious. Customers ought to be cautious when putting in such instruments, as they could comprise dangerous software program.
Safety Dangers of DNS Bypassing
Bypass strategies can expose customers to important safety dangers. Unverified DNS servers or improperly configured instruments can result in compromised accounts, malware infections, or knowledge breaches. A vital concern is the chance of interacting with malicious actors.
- Malware infections: Some bypass instruments or companies could also be malicious, infecting your machine with malware. This may steal your private data or management your machine remotely.
- Knowledge breaches: Utilizing unverified or insecure bypass companies can expose your delicate knowledge to unauthorized entry.
- Phishing assaults: Bypassing restrictions could make you extra susceptible to phishing makes an attempt, which intention to trick you into revealing private data.
- Authorized penalties: In some areas, bypassing DNS restrictions can have extreme authorized repercussions.
Authorized Implications of DNS Bypassing
The legality of DNS bypassing varies considerably by jurisdiction. In lots of areas, circumventing restrictions imposed by respectable authorities can result in authorized penalties. The particular rules depend upon the nation, the particular methodology used, and the character of the restrictions.
Moral Issues of DNS Bypassing
Moral issues are vital when utilizing DNS bypass strategies. Whereas bypassing restrictions may supply entry to blocked content material, it could violate the phrases of service of suppliers or probably violate the legislation.
- Respect for legal guidelines and rules: Customers ought to respect the legal guidelines and rules of the nations or areas the place they’re utilizing the web.
- Avoiding hurt to others: Customers ought to be aware that their actions can have penalties for others, comparable to spreading misinformation or facilitating unlawful actions.
- Defending private knowledge: Customers should prioritize the safety of their private knowledge when utilizing bypass strategies.
Authentic vs. Illegitimate DNS Utilization
| Function | Authentic DNS Utilization | Illegitimate DNS Utilization |
|---|---|---|
| Objective | Accessing approved content material, bettering community efficiency, and resolving domains. | Circumventing restrictions imposed by respectable authorities, accessing prohibited content material, and interesting in unlawful actions. |
| Strategies | Utilizing really useful DNS servers, configuring DNS settings, and using VPNs for respectable functions. | Utilizing unauthorized DNS servers, putting in malicious software program, and utilizing proxy servers to hide unlawful actions. |
| Safety | Typically secure and safe, using trusted suppliers. | Probably insecure and dangerous, utilizing untrusted companies or software program. |
| Authorized Implications | Typically compliant with native rules. | Probably violating native legal guidelines and rules. |
iCloud Entry and Authentication
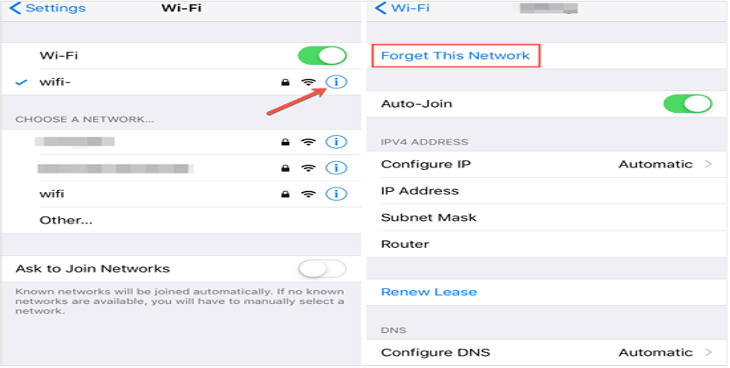
iCloud is a well-liked cloud storage service that allows you to entry your recordsdata from varied units. Securing entry to your iCloud knowledge is essential, and understanding the authentication course of is vital to defending your data. This part dives into the specifics of iCloud’s authentication strategies and the function DNS performs on this course of.The authentication course of for iCloud entails a number of steps, together with offering credentials like your Apple ID and password.
These credentials are used to confirm your id and grant entry to your iCloud knowledge. This verification typically makes use of a safe connection to Apple’s servers, additional enhancing the safety of your delicate data.
iCloud Authentication Course of
The authentication course of for iCloud sometimes entails a collection of steps designed to confirm your id and authorize entry to your knowledge. These steps typically embrace submitting your credentials, verifying their validity, and granting entry solely after profitable authentication.
- Preliminary Request: A consumer initiates the method by coming into their Apple ID and password when accessing iCloud companies on a tool or utility.
- Verification: Apple’s servers validate the offered credentials in opposition to their database, checking for matches and guaranteeing the knowledge is respectable.
- Authorization: If the credentials are right, Apple authorizes entry to the requested iCloud sources. This authorization typically entails a short lived token or session ID that is used to authenticate future requests.
- Safe Connection: Your complete course of sometimes takes place over a safe connection, like HTTPS, to guard your credentials from interception throughout transmission.
Position of DNS in iCloud Authentication
DNS, or Area Title System, performs an important function in resolving the domains utilized by iCloud companies. Whereas circuitously concerned within the authentication course of itself, DNS ensures that the consumer’s machine can attain the right iCloud servers. This decision occurs behind the scenes, facilitating the connection between the consumer and iCloud.
- Title Decision: Whenever you entry iCloud, your machine must find the suitable iCloud servers. DNS interprets the area title (e.g., icloud.com) into the numerical IP tackle of the related server.
- Safety Issues: DNS itself is not immediately chargeable for authentication. Nevertheless, safe DNS implementations can shield in opposition to malicious actors making an attempt to intercept or redirect the request to a fraudulent server.
Strategies of Accessing iCloud Knowledge
iCloud knowledge could be accessed by varied strategies, tailoring the consumer expertise throughout a number of units and platforms. These strategies guarantee compatibility and comfort for customers.
- Net Browser: Accessing iCloud by an online browser is a simple methodology. Customers can log in and handle their knowledge utilizing an online interface.
- Cellular Purposes: Devoted cell purposes present a streamlined consumer interface for accessing and managing iCloud knowledge on smartphones and tablets. These purposes leverage the machine’s working system to optimize consumer expertise.
- Desktop Purposes: Desktop purposes supply a richer consumer expertise for managing and interacting with iCloud knowledge on computer systems, offering a extra highly effective and customizable interface.
Step-by-Step iCloud DNS Lookup
This course of demonstrates how a DNS lookup happens when accessing iCloud.
- Request Initiated: A consumer makes an attempt to entry an iCloud service (e.g., iCloud Drive).
- DNS Question: The consumer’s machine sends a DNS question to a DNS resolver, requesting the IP tackle for the iCloud service.
- DNS Decision: The DNS resolver queries a DNS server to find the IP tackle comparable to the iCloud area.
- IP Handle Returned: The DNS server returns the IP tackle to the DNS resolver.
- Connection Established: The DNS resolver offers the IP tackle to the consumer’s machine, which then establishes a connection to the suitable iCloud server.
iCloud Safety Measures
iCloud employs varied safety measures to guard consumer knowledge. These measures are essential for safeguarding delicate data saved within the cloud.
| Safety Measure | Description |
|---|---|
| HTTPS | Makes use of safe protocols to encrypt communication between the consumer’s machine and iCloud servers. |
| Two-Issue Authentication (2FA) | Provides an additional layer of safety by requiring a second verification methodology, comparable to a code from a cell machine. |
| Knowledge Encryption | Encrypts consumer knowledge each in transit and at relaxation, defending it from unauthorized entry even when the information is compromised. |
| Common Safety Audits | iCloud commonly audits its methods to establish and tackle potential vulnerabilities, enhancing the general safety posture. |
Potential Vulnerabilities
DNS configurations, essential for iCloud entry, can harbor vulnerabilities. These weaknesses could be exploited by malicious actors to achieve unauthorized entry to iCloud accounts, probably resulting in knowledge breaches and id theft. Understanding these vulnerabilities and the way they are often exploited is crucial for safeguarding iCloud customers’ delicate data.Exploiting DNS vulnerabilities can result in a variety of points, from account hijacking to knowledge theft.
Realizing the kinds of vulnerabilities and the way they manifest is important for proactive protection and sturdy safety measures.
DNS Configuration Weaknesses
DNS servers, the phonebook of the web, translate domains into IP addresses. Improper configuration of those servers can go away them open to assaults. Misconfigured DNS information can redirect customers to malicious web sites masquerading as respectable iCloud login pages, resulting in credential theft. This misdirection, typically delicate, generally is a important safety danger.
Exploit Methods
Malicious actors can use varied methods to take advantage of DNS vulnerabilities associated to iCloud entry. These vary from easy DNS spoofing to extra complicated assaults leveraging DNS cache poisoning.
- DNS Spoofing: A malicious actor may redirect DNS queries for iCloud companies to a pretend server. This pretend server may mimic the respectable iCloud login web page, capturing consumer credentials as they’re entered.
- DNS Cache Poisoning: An attacker can inject false DNS information right into a DNS resolver’s cache. This may redirect respectable customers to malicious servers, compromising their safety. This system typically targets the intermediate DNS servers in a consumer’s request chain, making the assault more durable to detect.
- Man-in-the-Center Assaults: Attackers intercept DNS requests and responses. This permits them to control the communication between the consumer and the iCloud server. On this case, they may intercept the login credentials earlier than they attain the iCloud server, resulting in unauthorized entry.
Impression on iCloud Customers
DNS vulnerabilities can considerably affect iCloud customers. Compromised accounts result in potential knowledge breaches, lack of delicate data, and monetary losses. These breaches may embrace entry to images, paperwork, and different private knowledge.
Exploitation Strategies
A number of strategies are used to take advantage of DNS vulnerabilities. Attackers can leverage compromised methods, exploit configuration flaws, or use social engineering methods to trick customers into coming into credentials on pretend login pages.
Vulnerability Abstract
| Vulnerability Sort | Impression | Instance |
|---|---|---|
| DNS Spoofing | Redirecting customers to pretend iCloud login pages | Consumer unknowingly enters credentials on a malicious website that mimics iCloud’s login portal. |
| DNS Cache Poisoning | Redirecting customers to malicious servers | A consumer’s DNS resolver is poisoned, main them to a malicious website masquerading because the iCloud login web page. |
| Man-in-the-Center | Intercepting and manipulating communications | Attacker intercepts the communication between the consumer and the iCloud server, capturing login credentials. |
Different Entry Strategies
So, you have realized about DNS bypasses, however there are different methods to probably entry iCloud knowledge with out counting on probably dangerous or unlawful strategies. These different strategies, whereas typically extra easy, won’t all the time be as versatile or handy. Understanding their execs and cons is vital to creating an knowledgeable choice.
Legitimate iCloud Account Entry
That is probably the most easy and usually most secure strategy. When you’ve got a legitimate iCloud account with the right credentials, you may entry your knowledge by the official iCloud web site or apps. This methodology avoids any potential safety dangers related to bypassing safety measures. The steps are often fairly easy, and there are sources accessible for assist.
Utilizing iCloud Restoration Choices
If you happen to’ve forgotten your password or produce other account points, iCloud presents restoration choices. These instruments can assist you regain entry to your account when you observe the steps fastidiously. It is a respectable and official course of offered by Apple, and sometimes entails safety questions or restoration emails. It is a good different when you’ve misplaced entry to your account on account of a forgotten password or related points.
Utilizing Approved Third-Occasion Apps
Generally, third-party apps can present entry to iCloud knowledge, however solely with permission. These apps are sometimes designed for particular functions and will not be applicable for all eventualities. In case you are utilizing an app that’s appropriate along with your wants and you have given it permission to entry your iCloud knowledge, it could present an alternate entry methodology.
Utilizing a Backup or Restore Process
If you happen to’ve beforehand backed up your iCloud knowledge to a different machine or service, you may restore it. It is a good technique to retrieve your knowledge in case your main machine is misplaced or broken. This methodology assumes you could have a earlier backup and know the best way to restore from it.
So, you are trying to bypass iCloud DNS restrictions? Nicely, whereas some strategies may promise fast entry to issues like Kira Pregiato’s OnlyFans , do not forget that unauthorized entry to content material is commonly dangerous. Follow respectable and secure methods to entry on-line content material for a safer expertise when coping with DNS iCloud bypasses.
Comparability Desk of Different Entry Strategies, Dns icloud bypass
| Entry Technique | Benefits | Disadvantages | Steps Concerned |
|---|---|---|---|
| Legitimate iCloud Account Entry | Safe, respectable, easy | Requires legitimate credentials | Log in to iCloud web site or app with right username and password. |
| iCloud Restoration Choices | Official Apple process, typically dependable | Might require further safety measures (e.g., safety questions) | Comply with the iCloud account restoration steps, offering essential data. |
| Approved Third-Occasion Apps | Comfort for particular duties | Will not be appropriate for all knowledge, potential privateness considerations | Set up the app, authorize it to entry your iCloud knowledge. |
| Backup/Restore | Retrieves knowledge from earlier backups | Requires a earlier backup, potential knowledge loss if no backup exists | Establish backup location, observe restore directions from backup. |
Safety Finest Practices

Defending your iCloud account from DNS bypass assaults requires a multi-faceted strategy. These assaults exploit vulnerabilities in how your machine interacts with iCloud servers. Strong safety habits are your first line of protection. This part Artikels essential steps to safeguard your account.Sturdy safety measures are essential to forestall unauthorized entry. Your iCloud account is a worthwhile asset, containing private data and knowledge.
Sturdy safety practices are important to guard it from varied cyber threats.
Sturdy Passwords and Multi-Issue Authentication
Sturdy passwords are a elementary facet of account safety. A powerful password is exclusive, lengthy, and incorporates a mixture of uppercase and lowercase letters, numbers, and symbols. Keep away from utilizing simply guessed passwords, comparable to your title, birthday, or frequent phrases. Usually altering your password can also be advisable. Utilizing a password supervisor can tremendously help in creating and managing complicated passwords.Multi-factor authentication (MFA) provides an additional layer of safety.
When enabled, MFA requires a second type of verification, comparable to a code despatched to your telephone, past your password. This makes it considerably more durable for attackers to entry your account even when they get hold of your password. Allow MFA for all of your vital accounts, together with your iCloud account.
Safe Networks and Gadgets
Utilizing safe networks is paramount for safeguarding your iCloud account. Keep away from utilizing public Wi-Fi networks for delicate duties, comparable to accessing your iCloud account. Public networks typically lack correct safety measures, making your connection susceptible to eavesdropping. If you happen to should use public Wi-Fi, make the most of a VPN (Digital Personal Community) to encrypt your knowledge.Holding your units up to date is equally vital.
Software program updates typically embrace safety patches that tackle vulnerabilities. Usually updating your iOS machine, working system, and different purposes minimizes the chance of exploits.
Really useful Safety Measures
A complete safety technique entails a number of interconnected measures. A sturdy safety posture combines varied ways to discourage attackers and mitigate dangers.
- Allow Two-Issue Authentication (2FA): This provides an important layer of safety, requiring a secondary verification methodology past your password.
- Use a Sturdy Password Supervisor: A password supervisor generates and shops complicated passwords for you, eliminating the necessity to memorize them.
- Maintain Software program Up to date: Usually updating your iOS machine and purposes patches safety vulnerabilities.
- Keep away from Public Wi-Fi for Delicate Duties: Utilizing safe networks, like your property community, minimizes the chance of unauthorized entry.
- Use a VPN for Public Wi-Fi: Encrypting your reference to a VPN protects your knowledge whereas utilizing public Wi-Fi.
- Be Cautious of Phishing Makes an attempt: Be cautious of suspicious emails or messages asking in your login credentials.
- Monitor Account Exercise: Usually examine your account exercise for any uncommon login makes an attempt.
Configuring DNS Settings for Enhanced Safety
Configuring your DNS settings can additional improve the safety of your iCloud entry. This entails selecting a dependable DNS supplier and guaranteeing the settings are appropriately configured in your machine. A good DNS supplier presents larger safety and stability.
- Select a Dependable DNS Supplier: Go for a DNS supplier with a confirmed observe file of safety and reliability. Contemplate a supplier that provides enhanced security measures, comparable to superior menace safety.
- Configure DNS Settings on Your Machine: Make sure the DNS settings in your iOS machine are configured to make use of a safe and reliable DNS supplier. This may route your visitors by a safer path, minimizing vulnerabilities.
Actual-World Examples
DNS bypass makes an attempt concentrating on iCloud, whereas typically unsuccessful, have sometimes led to compromised accounts or service disruptions. These makes an attempt, typically pushed by malicious actors, spotlight the continuing want for sturdy safety measures in on-line companies. Understanding the specifics of those makes an attempt, profitable and unsuccessful, offers essential perception into the evolving panorama of cyber threats.Actual-world examples of DNS bypass makes an attempt in opposition to iCloud typically contain refined methods, starting from easy manipulation of DNS information to extra complicated exploits concentrating on vulnerabilities inside iCloud’s authentication processes.
The outcomes of those makes an attempt can differ broadly, relying on the sophistication of the assault and the resilience of the goal system.
Unsuccessful Bypass Makes an attempt
These makes an attempt typically fail on account of iCloud’s sturdy authentication mechanisms. Safety measures, together with multi-factor authentication and rigorous IP tackle validation, are designed to thwart many primary DNS bypass ways. For instance, a easy try and redirect DNS visitors to a malicious server is likely to be blocked by iCloud’s safety protocols, leading to failed login makes an attempt or entry denied errors.
These failed makes an attempt typically function studying alternatives for each attackers and defenders, refining safety protocols and assault strategies.
Profitable Bypass Makes an attempt (Restricted and Uncommon)
Profitable bypasses are extraordinarily uncommon, typically involving extremely specialised methods. These exploits sometimes goal vulnerabilities in particular configurations or outdated methods, comparable to weak or default passwords on the consumer’s aspect or configurations that permit for bypassed verification processes. Generally, the success is short-lived as a result of swift patching of vulnerabilities by iCloud’s safety workforce. These uncommon examples exhibit the significance of constant safety updates and vigilant monitoring of potential exploits.
Impression on People and Organizations
Unsuccessful makes an attempt may lead to irritating experiences for people making an attempt to entry their iCloud accounts. These makes an attempt may lead to elevated safety consciousness and a greater understanding of the significance of robust passwords and safety practices. Profitable makes an attempt, whereas uncommon, can result in important knowledge breaches or account compromises. This might contain the theft of non-public data, monetary losses, or reputational harm for people or organizations.
Impression Abstract Desk
| Try End result | Impression on People | Impression on Organizations |
|---|---|---|
| Unsuccessful | Frustration, heightened safety consciousness | Enhanced safety protocols, improved incident response |
| Profitable (Uncommon) | Knowledge breach, monetary loss, reputational harm | Knowledge breaches, monetary losses, authorized ramifications |
Wrap-Up
In conclusion, DNS iCloud bypass presents a multifaceted problem with important safety implications. Whereas understanding the strategies for bypassing restrictions could be worthwhile, it is equally vital to prioritize safety and discover different entry strategies. By understanding the potential vulnerabilities and adopting robust safety practices, you may safeguard your iCloud account and knowledge.
FAQ Nook: Dns Icloud Bypass
What are some different strategies for accessing iCloud knowledge in addition to DNS bypass?
Different strategies embrace utilizing a VPN, logging in by a trusted machine, or utilizing the iCloud net portal. Every methodology has its personal set of benefits and drawbacks.
What are the potential safety dangers of bypassing DNS settings?
Bypassing DNS settings can expose your account to unauthorized entry, knowledge breaches, and malware infections. That is typically a violation of phrases of service and will result in account suspension or authorized points.
What are the authorized implications of utilizing DNS bypass strategies?
Utilizing DNS bypass strategies could violate phrases of service or relevant legal guidelines. Unauthorized entry to iCloud accounts is prohibited and will result in authorized repercussions.
How can I configure my DNS settings for enhanced safety?
Configuring your DNS settings for enhanced safety entails utilizing robust passwords, enabling multi-factor authentication, and utilizing safe networks. All the time replace your software program to patch identified vulnerabilities.
