iPhone location spoofing strategies assist you to trick apps and providers into pondering your telephone is in a unique place. This can be utilized for gaming, social media, and even safety functions. However what are the alternative ways to do that? And what are the dangers?
This information explores the assorted methods behind location spoofing on iPhones, from the easy to the advanced. We’ll delve into the technical particulars, focus on potential vulnerabilities, and look at tips on how to detect and stop these spoofing strategies. We’ll additionally contact on the authorized and moral elements, and take a look at potential future developments within the area.
Introduction to Location Spoofing
Location spoofing is the act of tricking a tool or software into believing your present location is totally different from the precise one. It is basically faking your GPS coordinates. This may be accomplished on varied units, like smartphones, and utilized in a shocking variety of methods.This system is more and more widespread in trendy life, from gaming to safety issues. Understanding its varied functions and potential implications is essential for anybody who makes use of location-aware providers.
Moreover, greedy the moral and authorized ramifications is essential for accountable use of know-how.
Completely different Contexts of Location Spoofing
Location spoofing is utilized in quite a lot of contexts. Gaming is a typical software, the place gamers can nearly be elsewhere or occasions to achieve benefits. On social media, it may be used for varied causes, equivalent to making a false sense of presence or to bypass geographic restrictions. Safety makes use of embrace testing and analysis of safety methods, nevertheless it’s additionally regularly employed for malicious actions, equivalent to fraud or harassment.
Motivations Behind Location Spoofing
Individuals spoof their location for a variety of causes. Some motivations are benign, equivalent to gaming benefits or testing providers. Others are malicious, aiming for fraud, harassment, or bypassing restrictions. There are additionally extra delicate motivations, like hiding private areas for privateness causes or taking part in digital occasions.
Authorized and Moral Implications
Location spoofing has important authorized and moral implications. In some contexts, it may be thought-about a violation of phrases of service and even unlawful, notably if it results in fraud, harassment, or different malicious actions. Moral issues embrace respecting privateness, avoiding deception, and never inflicting hurt or disruption to others.
Sorts of Location Spoofing Strategies
- Community-based spoofing: This methodology entails manipulating the community indicators or routing to trick the machine into pondering it is in a unique location. It usually entails utilizing a VPN or proxy server to alter the obvious location of the machine. This methodology is comparatively easy to arrange, however its effectiveness is determined by the machine and community circumstances.
- GPS sign manipulation: This methodology focuses on interfering with or altering the GPS indicators acquired by the machine. This may be accomplished by creating pretend GPS indicators or jamming present ones. This methodology requires specialised tools and is commonly extra advanced to implement than network-based spoofing.
- Software-level spoofing: On this method, the spoofing is completed inside the software itself, manipulating the placement information reported by the app with out straight altering the GPS coordinates. It is regularly utilized in gaming or social media contexts to create digital experiences.
Comparability of Location Spoofing Strategies
| Methodology | Complexity | Effectiveness | Moral Issues |
|---|---|---|---|
| Community-based | Low | Average | Probably low if used responsibly |
| GPS sign manipulation | Excessive | Excessive (if profitable) | Excessive threat of misuse |
| Software-level | Average | Average to excessive, relying on the app | Depends upon the appliance’s phrases of service |
Frequent iPhone Location Spoofing Strategies
Location spoofing on iPhones, whereas usually related to malicious intent, may also be used for reliable functions like gaming or testing. Understanding the totally different strategies, their technical underpinnings, and related dangers is essential for each customers and builders. This part delves into the widespread methods employed for location spoofing on iPhones.Frequent strategies of location spoofing on iPhones exploit varied system vulnerabilities and functionalities.
These vary from easy manipulations of mobile information to extra subtle methods involving app-level modifications. Understanding these methods permits for higher consciousness and potential mitigation methods.
Mobile Community Spoofing
This methodology leverages the iPhone’s mobile community to simulate a unique location. The telephone basically tips the GPS system by offering false community information.
- Instance: A person could be positioned in a particular space with a selected cell tower sign. By spoofing their cell tower location, they may seem like in a unique geographic space.
- Technical Precept: The iPhone communicates with cell towers to find out its location. Spoofing entails manipulating this communication, doubtlessly through the use of a modified SIM card or a proxy server to obtain false location info from the mobile community.
- Instruments and Software program: SIM card spoofing instruments, proxy servers, and custom-built functions are regularly used.
- Vulnerabilities: The accuracy of this methodology relies upon closely on the cell tower information out there, and it may be much less exact than GPS-based strategies. Safety flaws within the mobile community infrastructure is also exploited. Furthermore, some cellular carriers have anti-spoofing measures in place.
GPS Spoofing
This system straight alters the GPS sign acquired by the machine.
- Instance: An app may modify the GPS sign, tricking the telephone into reporting a location totally different from the precise one.
- Technical Precept: GPS depends on indicators from satellites to find out place. Spoofing entails sending false GPS indicators to the machine, doubtlessly utilizing a specialised machine or software program to intervene with the GPS sign. This usually entails manipulating the timing or energy of the indicators.
- Instruments and Software program: Specialised {hardware} for jamming GPS indicators, or subtle functions designed to inject false GPS information.
- Vulnerabilities: The success of GPS spoofing usually is determined by the energy of the sign and the precision of the false sign. Furthermore, there are sometimes anti-spoofing measures constructed into GPS receivers and working methods.
Wi-Fi Spoofing
This methodology makes use of Wi-Fi indicators to deduce a location.
- Instance: A person may spoof their Wi-Fi sign to look as in the event that they’re linked to a Wi-Fi community in a unique space.
- Technical Precept: Wi-Fi networks have distinctive identifiers (MAC addresses) and related areas. Spoofing entails altering the machine’s Wi-Fi MAC tackle or connecting to a Wi-Fi community in a unique location, creating the impression of a unique location. This methodology is much less exact than GPS or mobile strategies.
- Instruments and Software program: Instruments that manipulate Wi-Fi community info and software program that may change a tool’s MAC tackle.
- Vulnerabilities: The accuracy and reliability of this methodology rely closely on the accuracy of the Wi-Fi location information out there. Moreover, some Wi-Fi networks have safety measures to forestall spoofing makes an attempt.
Software-Stage Spoofing
Some functions may present a technique to manually set or override the machine’s location.
- Instance: A sport may enable customers to alter their location for in-game functions. This usually has built-in performance.
- Technical Precept: These functions usually have direct entry to the machine’s location providers. Spoofing can happen via modification of the appliance’s code, permitting the person to override the placement service’s regular operate.
- Instruments and Software program: Software program or instruments that enable for direct manipulation of the placement providers APIs.
- Vulnerabilities: The safety of those strategies is determined by the appliance itself. Malicious functions may exploit this performance to misrepresent location for malicious intent.
Steps Concerned in Location Spoofing (Illustrative Desk)
| Methodology | Step 1 | Step 2 | Safety Implications |
|---|---|---|---|
| Mobile Community Spoofing | Establish goal cell tower location | Manipulate mobile community information to replicate spoofed location | Potential for privateness violations, unauthorized entry, and fraud |
| GPS Spoofing | Generate false GPS indicators | Inject false indicators into the machine’s GPS receiver | Potential for location monitoring, manipulation of GPS-dependent providers, and safety dangers |
| Wi-Fi Spoofing | Modify machine’s Wi-Fi MAC tackle or connect with a spoofed Wi-Fi community | Make the most of Wi-Fi community info to supply a spoofed location | Potential for unauthorized entry to Wi-Fi networks and location-based providers |
| Software-Stage Spoofing | Modify the appliance’s code or entry to location providers APIs | Override or set a false location inside the software | Potential for privateness violations, safety breaches inside the software, and unauthorized entry to location information |
Technical Particulars of Spoofing Strategies

Location spoofing is not nearly tricking apps; it is about manipulating the indicators your telephone makes use of to find out its place. Understanding the underlying mechanisms of those tips is vital to comprehending the potential dangers and the way spoofing works. Completely different strategies goal totally different elements of your telephone’s location providers, from GPS to mobile networks.The varied strategies contain subtly altering or faking information streams that your telephone makes use of to calculate its place.
This manipulation will be advanced, however understanding the fundamentals helps to acknowledge how these methods work.
GPS Spoofing
GPS spoofing entails tricking your telephone into pondering it is receiving indicators from pretend GPS satellites. These pretend indicators will be designed to put your machine anyplace on a map. This system normally requires specialised {hardware} and software program to generate and transmit the false GPS indicators. The accuracy and effectiveness of GPS spoofing usually rely on the standard and precision of the pretend indicators generated, and the way successfully they will masks their synthetic nature.
Mobile Community Spoofing
Mobile community spoofing leverages the truth that your telephone’s location is commonly decided by its cell tower proximity. Spoofing can create a false sense of proximity to totally different cell towers, thus deceptive the telephone into reporting a location apart from the precise one. This methodology will be fairly efficient as a result of cell towers are sometimes dense and simply manipulated, which is why this methodology is regularly utilized in mixture with different spoofing methods.
Critically, the effectiveness of mobile spoofing is determined by the entry and management over the mobile community.
Wi-Fi Spoofing
Wi-Fi spoofing entails creating pretend Wi-Fi entry factors to trick your telephone into believing it is linked to a community at a unique location. The telephone then makes use of the detected Wi-Fi sign’s location to estimate its personal. This system usually entails both making a pretend community or altering the placement info reported by a real community. These approaches are much less subtle than GPS spoofing however nonetheless efficient for native location spoofing.
The complexity of this method is relative to the entry and manipulation of the Wi-Fi community indicators.
VPN for Location Spoofing
VPNs can be utilized to spoof your location by routing your web site visitors via a server in a unique geographical space. The telephone’s location providers might replace their place to the server’s location. Nonetheless, this methodology is not at all times foolproof. Safety issues come up when utilizing a VPN for spoofing as a result of it depends on a 3rd get together, and the VPN’s trustworthiness and safety practices are important.
Moreover, some apps are designed to detect VPN utilization and doubtlessly block location spoofing makes an attempt.
Proxy Servers for Location Spoofing
Proxy servers act as intermediaries between your telephone and the web. Some proxy servers might report a unique location than your precise one, thereby spoofing your location. The effectiveness of this methodology is determined by the proxy server’s configuration and the precise apps or providers used. Nonetheless, like VPNs, proxy servers can expose safety vulnerabilities if not used rigorously.
The safety and reliability of the proxy server are essential for profitable location spoofing.
Bluetooth Spoofing
Bluetooth spoofing works by manipulating the Bluetooth indicators your telephone sends and receives. This methodology can trick your telephone into believing it is linked to units at a unique location. By imitating the indicators, your telephone’s location providers might replace their place to the placement of the spoofed Bluetooth machine. The sophistication and success of this methodology usually rely on the power to imitate the Bluetooth indicators precisely and successfully.
Detection and Prevention of iPhone Location Spoofing
Recognizing pretend location information on an iPhone is essential for sustaining correct monitoring and stopping malicious exercise. This part delves into how apps and methods can determine and thwart makes an attempt to control location info.Understanding the strategies used to detect spoofing is crucial for builders and customers alike. Strong detection and prevention mechanisms are important in right now’s interconnected world, the place location-based providers are integral to quite a few functions.
Strategies for Detecting Location Spoofing
Varied methods exist to detect fraudulent location information. Apps and units make use of numerous strategies to confirm the authenticity of reported areas. These methods usually contain evaluating the reported location with different information sources, analyzing patterns of motion, and assessing the plausibility of the reported coordinates.
Software-Stage Detection Methods
Apps can make use of a number of methods to determine potential location spoofing. As an example, they may examine for uncommon or speedy modifications in location, examine reported areas in opposition to identified landmarks or factors of curiosity, or consider the reported location’s proximity to mobile towers or Wi-Fi entry factors. A vital facet of app-level detection is contemplating the person’s typical motion patterns.
System-Stage Detection Methods
Units themselves can make use of subtle strategies for figuring out location spoofing. One method entails monitoring the machine’s inside sensors, like GPS, Wi-Fi, and mobile indicators, to determine inconsistencies or discrepancies. One other methodology analyzes the reported location’s accuracy and consistency over time. Moreover, units can cross-reference reported areas with identified geographic information, equivalent to highway networks and bodily buildings.
Technical Approaches for Stopping Location Spoofing
Stopping location spoofing requires a multi-layered method. A key part is to strengthen the safety protocols of the underlying location providers, together with authentication mechanisms and encryption. Moreover, steady updates to location detection algorithms are very important.
iPhone location spoofing is a fairly widespread factor, however if you happen to’re utilizing it for shady functions, you can get into authorized bother, like a possible lien sue on OnlyFans accounts. Take a look at the main points on how a lien sue on OnlyFans accounts may work here. Principally, perceive that whereas location spoofing itself is not inherently unlawful, utilizing it for fraudulent actions may result in critical repercussions.
So, watch out and use it responsibly.
Abstract of Detection Methods
| Detection Method | Description | Limitations |
|---|---|---|
| GPS Sign Evaluation | Examines GPS sign energy, accuracy, and satellite tv for pc visibility. | Might be circumvented with robust GPS spoofing indicators. |
| Mobile Tower Proximity | Compares reported location with close by mobile towers. | Accuracy is determined by tower density and sign energy. |
| Wi-Fi Entry Level Evaluation | Analyzes reported location relative to identified Wi-Fi entry factors. | Effectiveness is determined by Wi-Fi protection. |
| Motion Sample Evaluation | Evaluates the reported location’s consistency with typical person motion. | Requires establishing baseline person conduct patterns. |
Advisable Practices for Securing Location Knowledge
Sustaining the integrity of location information necessitates a proactive method. Customers must be cautious about granting location entry to functions, solely granting permission when completely essential. Moreover, they need to often evaluate and replace the privateness settings of location providers.
- Frequently evaluate app permissions: Customers ought to periodically evaluate which functions have entry to their location information and revoke permissions for any pointless or untrusted apps.
- Make use of robust machine safety: Sustaining a robust machine password, enabling two-factor authentication, and putting in safety updates is significant in mitigating potential vulnerabilities. This additionally protects in opposition to different types of spoofing and hacking.
- Be cautious of phishing makes an attempt: Phishing assaults can exploit location providers to deceive customers. Train warning when clicking hyperlinks or putting in functions from unknown sources.
Safety In opposition to Varied Spoofing Assaults
Strong protection methods are essential in countering varied spoofing methods. For instance, using subtle filtering algorithms can decrease the influence of GPS spoofing. Furthermore, constantly updating location detection software program with the most recent anti-spoofing methods is crucial. Moreover, educating customers about potential spoofing makes an attempt and selling safe practices can considerably strengthen general safety.
Case Research and Actual-World Examples
Location spoofing is not only a enjoyable trick; it has critical penalties in the actual world. From monetary fraud to felony exercise, the power to pretend your location will be weaponized in some ways. Understanding these examples is essential for recognizing and stopping the misuse of this know-how.This part delves into varied cases of location spoofing, highlighting its use in fraudulent schemes, felony actions, and even much less apparent eventualities.
We’ll discover how perpetrators leverage this know-how, emphasizing the potential hurt and the way victims can shield themselves.
Penalties of Location Spoofing
Location spoofing can result in important monetary losses and authorized repercussions for the perpetrators. One widespread consequence is the fraudulent use of location information to make unauthorized transactions or entry providers. A sufferer may discover their checking account drained or their private info compromised consequently.
Fraudulent Schemes
Location spoofing is regularly employed in fraudulent schemes concentrating on varied providers and companies. For instance, a scammer may use spoofing to put orders or request refunds from e-commerce websites beneath false pretenses. They might additionally try to say fraudulent refunds or advantages from subscription providers, utilizing a spoofed location to disguise their actions.
Felony Actions
Criminals might use location spoofing to evade legislation enforcement, conduct unlawful actions, or acquire entry to restricted areas. They could use a spoofed location to hide their true whereabouts, doubtlessly for drug trafficking, financial institution theft, or different critical offenses.
Authorized and Moral Makes use of (If Any)
Whereas spoofing is primarily related to adverse penalties, there are some restricted moral makes use of. For instance, it could possibly be utilized by journalists to guard their sources, or in some particular conditions by legislation enforcement businesses for surveillance or investigations. Nonetheless, these functions are extraordinarily restricted, and the potential for misuse usually outweighs the perceived advantages.
Desk of Examples
| Case | Location | Time | Influence |
|---|---|---|---|
| Unauthorized ATM Withdrawal | Metropolis A, ATM close to sufferer’s dwelling | Evening, 2:00 AM | $500 withdrawn from sufferer’s account. |
| Pretend Supply | Sufferer’s dwelling | Afternoon, 1:00 PM | Spoofed location results in a supply of counterfeit items. |
| Insurance coverage Fraud | Accident location (totally different state) | Late night time | Sufferer claims insurance coverage advantages from an accident that did not happen. |
| Unlawful Streaming | Geo-restricted area | Varied occasions | Person spoofs location to entry geo-restricted streaming content material. |
Future Developments and Developments
Location spoofing is consistently evolving, fueled by developments in know-how and the growing reliance on location-based providers. Anticipating these modifications is essential for each builders and customers to remain forward of potential points and vulnerabilities. This part explores the potential way forward for location spoofing, together with rising methods, countermeasures, and the influence on varied industries.
Potential Future Developments in Spoofing Expertise
Future location spoofing methods will probably leverage extra subtle strategies to bypass present detection mechanisms. These embrace using extra superior emulators, harnessing the ability of cloud-based providers for advanced spoofing operations, and doubtlessly integrating spoofing capabilities into on a regular basis units, like smartwatches and even embedded in IoT units. Moreover, there is a risk of creating spoofing instruments that may dynamically regulate location information in real-time primarily based on person enter or exterior triggers.
Rising Spoofing Methods
Rising methods may contain spoofing indicators through the use of extremely specialised {hardware}, or leveraging new applied sciences like 5G and even 6G to boost spoofing capabilities. One other risk is the event of extra subtle sign manipulation methods, doubtlessly utilizing subtle sign jammers or different sign alteration strategies. The flexibility to imitate a large number of GPS units concurrently, doubtlessly via a community of compromised units, can also be a practical risk.
Countermeasures to Future Spoofing Strategies, Iphone location spoofing strategies
Efficient countermeasures in opposition to future spoofing strategies would require a multi-faceted method. This contains continually updating and refining location verification protocols. Growing strategies that may distinguish between real and spoofed indicators, doubtlessly by analyzing sign patterns or machine conduct, is important. Elevated cooperation between know-how corporations, legislation enforcement, and even regulatory our bodies can also be important to successfully fight the menace.
So, you’ve got messed round with iPhone location spoofing strategies, and now you are caught with a clean display screen or misplaced information. Do not panic! Knowledge restoration for iPhones like data recovery iphone can usually assist you to get your recordsdata again, however be warned, some spoofing strategies may make restoration tougher. Simply bear in mind, cautious dealing with of your telephone’s location settings is vital to keep away from these points within the first place.
Influence on Completely different Sectors
Location spoofing may have a wide-ranging influence on varied sectors. Monetary transactions, authorized proceedings, and even emergency providers could possibly be jeopardized by fraudulent location information. The transportation business, particularly ride-sharing and logistics, may face important disruptions as a result of inaccurate monitoring and supply points. Moreover, points with location-based promoting and customized providers may emerge.
Projected Influence on Industries
| Trade | Potential Influence |
|---|---|
| Monetary Providers | Elevated threat of fraudulent transactions, problem in verifying areas for monetary actions, potential for embezzlement, and substantial monetary losses. |
| Transportation | Disruptions in logistics, inaccurate supply occasions, fraudulent ride-sharing actions, and potential for accidents. |
| Regulation Enforcement | Difficulties in monitoring suspects, unreliable location information in investigations, and potential misallocation of assets. |
| E-commerce | Potential for fraudulent returns and transport, points with correct order monitoring, and potential injury to fame. |
| Healthcare | Difficulties in monitoring sufferers, potential for inaccurate emergency response occasions, and security issues concerning location-based medical providers. |
Final Recap
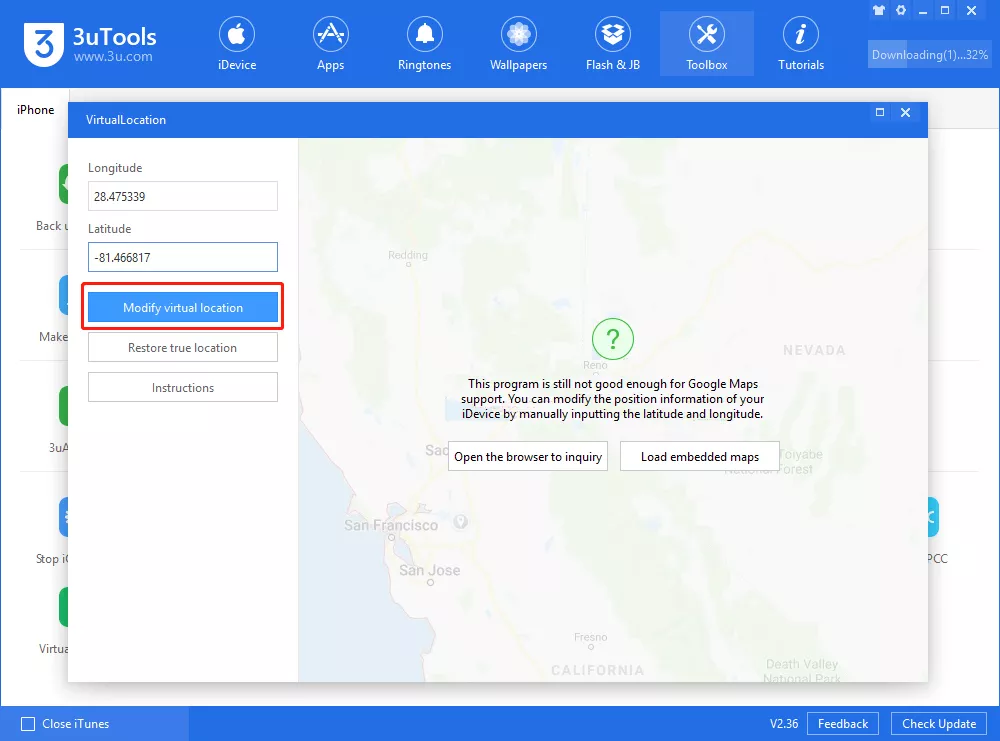
In conclusion, iPhone location spoofing provides a variety of capabilities, nevertheless it’s essential to grasp the safety implications and moral issues. Whereas there are reliable makes use of, misuse can result in critical issues. Understanding how these strategies work, tips on how to detect them, and the potential future developments is vital to staying secure in a digitally linked world.
Regularly Requested Questions
What are some widespread motivations for utilizing iPhone location spoofing?
Individuals may wish to play video games in a unique location, fake they’re someplace else for social media functions, or doubtlessly use it to bypass geographical restrictions.
What are the authorized implications of location spoofing?
Location spoofing can have authorized implications relying on the context. Misuse, like for fraud or unlawful actions, can have critical penalties.
Are there any dependable methods to detect location spoofing?
Purposes and units can detect location spoofing via varied strategies, together with checking for inconsistencies in location information or utilizing GPS sign energy evaluation.
Can VPNs be used for location spoofing?
Sure, VPNs can be utilized to spoof location, however this could create vulnerabilities, making your location tougher to confirm.
