ROM FRP bypass is a technique for unlocking Android gadgets which have Manufacturing facility Reset Safety (FRP) enabled. This entails circumventing safety measures to achieve entry to a tool’s working system, usually after a manufacturing unit reset or gadget theft. Understanding the intricacies of those bypass strategies, from the strategies used to the potential dangers, is essential for each customers and producers alike.
This detailed information explores the assorted strategies of ROM FRP bypass, analyzing their effectiveness, complexities, and moral implications. We’ll delve into the several types of bypass strategies, the safety vulnerabilities they exploit, and the way producers can shield towards them. Finally, this dialogue goals to offer a complete overview of this often-complex subject.
Understanding the Time period “ROM FRP Bypass”
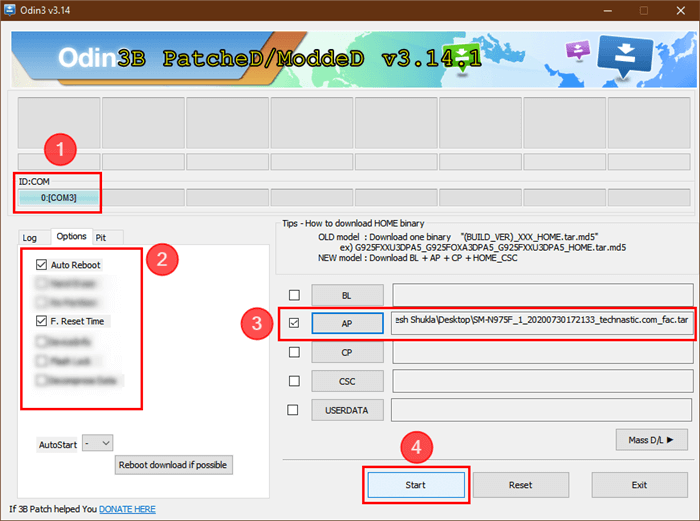
A ROM FRP bypass is a technique used to bypass Manufacturing facility Reset Safety (FRP) on a cell gadget. FRP is a safety measure applied by Android to forestall unauthorized entry after a manufacturing unit reset. This safety requires the consumer to log in with the unique Google account to entry the gadget. A ROM FRP bypass, due to this fact, goals to bypass this verification course of.This usually entails modifying the gadget’s software program (the ROM) to bypass the FRP test.
This usually entails customized ROMs or specialised instruments designed to use vulnerabilities or bypass the verification course of. Basically, it is a technique to get previous the preliminary setup display with out utilizing the unique Google account.
Definitions of FRP (Manufacturing facility Reset Safety)
Manufacturing facility Reset Safety (FRP) is a safety function applied in Android to forestall unauthorized entry to a tool after a manufacturing unit reset. That is achieved by requiring the consumer to log in with the unique Google account to unlock the gadget. This prevents stolen or misplaced gadgets from being simply accessed by others.
Completely different Kinds of ROM FRP Bypass Strategies
Numerous strategies exist for bypassing FRP utilizing ROM modifications. Some widespread strategies embrace:
- Kernel-level modifications: These modifications usually contain altering the gadget’s kernel to bypass the FRP test. This may be finished by modifying the kernel’s supply code or through the use of specialised kernel modules. These modifications are sometimes very particular to a specific gadget mannequin and require in-depth data of the gadget’s structure.
- Customized ROMs with embedded bypasses: Some customized ROMs are designed particularly to incorporate FRP bypass options. These ROMs usually have pre-built instruments or scripts to routinely bypass the FRP verification in the course of the preliminary setup course of. This strategy simplifies the method for customers but additionally probably introduces safety vulnerabilities relying on the ROM’s supply and safety practices.
- Third-party instruments and utilities: Particular instruments or utilities could also be used along side customized ROMs or different strategies to help within the FRP bypass course of. These instruments can vary from easy scripts to advanced software program packages, and their effectiveness and security range significantly.
Historic Context and Evolution of Bypass Strategies
FRP bypass strategies have developed alongside the sophistication of Android safety measures and the creativity of builders looking for to bypass them. Initially, easy exploits have been used to bypass the verification course of. As Android’s safety improved, bypass strategies grew to become extra advanced, usually counting on vulnerabilities throughout the Android working system or particular gadget {hardware}. This fixed arms race between safety and bypass strategies continues.
Potential Dangers Related to ROM FRP Bypass
Utilizing ROM FRP bypass strategies can carry vital dangers:
- System instability: Modifying the gadget’s ROM can result in instability and malfunctions. This could vary from minor glitches to finish gadget failure.
- Safety vulnerabilities: The method of bypassing FRP usually introduces safety vulnerabilities into the gadget, probably exposing it to malware or different malicious actions. It is a severe concern, particularly if the bypass just isn’t correctly applied or examined.
- Voiding guarantee: Modifying the gadget’s software program usually voids the gadget’s guarantee, leaving the consumer with no recourse if points come up after the modification.
- Authorized implications: In some instances, utilizing ROM FRP bypass strategies might violate the phrases of service or legal guidelines, probably resulting in authorized points.
Categorization of ROM FRP Bypass Strategies
ROM FRP bypass strategies may be categorized in a number of methods:
| Class | Description |
|---|---|
| Goal System Sort | Strategies may be tailor-made for particular gadget fashions or manufacturers, usually requiring particular modifications or exploits. |
| Bypass Technique | Strategies may be categorized by the particular method used, similar to kernel modifications, customized ROMs, or third-party instruments. |
| Complexity | Bypass strategies can range considerably in complexity, from easy scripts to superior strategies requiring in-depth data of the gadget’s software program and {hardware}. |
Strategies and Strategies
ROM FRP bypasses are achieved by way of numerous strategies, every with its personal strengths and weaknesses. Understanding these strategies permits customers to make knowledgeable selections about the very best strategy for his or her particular scenario. These strategies usually exploit vulnerabilities within the Android working system’s safety mechanisms.A key consideration when selecting a bypass technique is its effectiveness, which will depend on the particular Android model and gadget mannequin.
Some strategies may work on older gadgets however not on newer ones, and vice versa. Furthermore, the effectiveness of a way can fluctuate relying on the safety patches utilized to the goal gadget.
Frequent FRP Bypass Strategies
Completely different strategies goal numerous facets of the FRP lock. Some strategies concentrate on exploiting vulnerabilities within the system’s authentication course of, whereas others contain bypassing the preliminary setup altogether. The commonest strategies embrace exploiting software program bugs, using customized restoration modes, and using specialised instruments.
Exploiting Software program Bugs
Sure Android variations include flaws that may be leveraged to bypass FRP. These vulnerabilities may reside within the system’s authentication or setup routines. This technique depends on discovering and exploiting these vulnerabilities. Exploits usually contain modifying particular system information or injecting malicious code. Discovering and implementing these exploits requires superior technical data.
Using Customized Restoration Modes
Customized restoration modes are different bootloaders that may grant entry to the system past the conventional Android interface. They permit modifications and execution of instructions that bypass the FRP lock. This strategy usually entails flashing customized restoration photographs onto the gadget’s storage. This usually entails particular directions and cautious preparation to forestall information loss or bricking the gadget.
Using Specialised Instruments
Specialised instruments, usually developed by third-party builders, can streamline the FRP bypass course of. These instruments can automate elements of the method, probably simplifying the bypass for customers with restricted technical expertise. They usually leverage completely different strategies, similar to exploiting software program bugs or using customized restoration modes, to attain the bypass. These instruments are continuously up to date to keep up their effectiveness towards the most recent Android safety updates.
Comparability of Bypass Strategies
Completely different FRP bypass strategies supply various ranges of issue and danger. The complexity of the method instantly influences the potential for damaging the gadget. Strategies involving customized restoration modes, as an illustration, are usually extra advanced than exploiting software program bugs.
| Technique | Professionals | Cons | Complexity |
|---|---|---|---|
| Exploiting Software program Bugs | Probably simpler to implement with acceptable data. | Requires detailed data of system vulnerabilities and potential for vital danger of bricking. | Medium |
| Customized Restoration Modes | Presents better management over the gadget and might probably bypass extra superior safety measures. | Greater danger of information loss and bricking the gadget. Requires particular data and cautious execution. | Excessive |
| Specialised Instruments | Streamlines the method and reduces the complexity for customers with restricted technical data. | Could also be much less dependable than customized options, and will require ongoing updates to stay efficient. Instruments might change into outdated. | Low to Medium |
Authorized and Moral Issues
ROM FRP bypass, whereas seemingly a handy answer, raises vital authorized and moral issues. Customers should concentrate on the potential repercussions of using these strategies. The legality and moral implications range considerably relying on the particular jurisdiction and the circumstances surrounding the bypass.Using ROM FRP bypass strategies can result in severe authorized penalties, starting from fines to legal fees.
Understanding these implications is essential for accountable use of those instruments. Moreover, the moral issues surrounding unauthorized entry to cell gadgets are equally necessary.
So, you are trying to bypass FRP on a ROM? Generally, discovering the suitable assets may be tough. Try this search question for potential unlocked content material or streams associated to “intitle:mamaplugs” (stream or content material or unlocked or pack) intitle:”mamaplugs” (stream or content or unlocked or pack) to see if that helps together with your ROM FRP bypass.
Hopefully, you may discover some helpful data that will help you out together with your ROM bypass.
Authorized Implications of ROM FRP Bypass
The legality of ROM FRP bypass is very context-dependent. It is not universally unlawful, however in lots of jurisdictions, it is thought of a violation of phrases of service, mental property rights, or different rules. This could range considerably primarily based on the particular legal guidelines of every nation. Unauthorized entry to a tool, notably one containing delicate data, may be thought of a criminal offense in lots of jurisdictions.
Moral Issues Relating to Unauthorized Entry
Using ROM FRP bypass strategies usually entails unauthorized entry to a cell gadget, probably violating the proprietor’s privateness and safety. This motion compromises the gadget’s safety and might result in the publicity of delicate information. Moreover, it might be argued as unethical in that it disregards the proprietor’s rights to manage their gadget. Respect for the proprietor’s property rights is essential.
Potential Penalties for Customers
Customers who make use of ROM FRP bypass strategies face numerous potential penalties, relying on the particular jurisdiction and the circumstances. These can embrace hefty fines, imprisonment, and harm to their status. Furthermore, the safety vulnerabilities launched by unauthorized entry might expose the consumer to additional dangers. It is necessary to weigh the potential advantages towards the numerous authorized and moral dangers.
Comparability of Authorized and Moral Implications Throughout Jurisdictions
| Jurisdiction | Authorized Standing | Moral Issues |
|---|---|---|
| United States | Usually, bypassing FRP locks is taken into account a violation of the gadget producer’s phrases of service. Relying on the particular actions taken, it might additionally represent unauthorized entry, probably resulting in authorized motion. | Unauthorized entry to a cell gadget, particularly one with private information, is ethically questionable. This motion disregards the proprietor’s proper to manage their gadget and probably compromises their privateness. |
| European Union | Legal guidelines concerning unauthorized entry and mental property rights range throughout member states. Bypassing FRP locks may be thought of a violation of those rights, resulting in potential authorized repercussions. | The EU emphasizes consumer rights and information privateness. Unauthorized entry to a tool and its information is ethically problematic within the context of the EU’s information safety rules. |
| China | Particular legal guidelines and rules concerning ROM FRP bypass aren’t available in a concise format. Nonetheless, unauthorized entry to gadgets, particularly these containing delicate data, is prone to be thought of a violation of related legal guidelines. | Respect for consumer rights and information privateness is necessary in China. Bypassing FRP locks raises moral issues about unauthorized entry and potential privateness violations. |
Safety Vulnerabilities
ROM FRP bypass exploits weaknesses in Android’s manufacturing unit reset safety (FRP) system. These vulnerabilities usually stem from flaws within the gadget’s firmware or software program interactions. Understanding these weaknesses is essential for comprehending the dangers related to such bypass strategies and growing higher safety measures.
Exploited Firmware Weaknesses
The core of ROM FRP bypass lies in exploiting particular vulnerabilities throughout the gadget’s firmware. These vulnerabilities are sometimes present in the way in which the gadget’s working system interacts with the Google account tied to the gadget. For instance, a weak spot may exist in how the gadget authenticates the consumer’s Google account in the course of the preliminary setup course of.
Particular Concentrating on of Weaknesses
ROM FRP bypass strategies usually goal vulnerabilities within the Android framework, the Google Play Companies, or the gadget’s {hardware} drivers. The strategies may contain manipulating system calls, exploiting bugs in libraries, or tricking the system into believing a unique account is genuine. These strategies usually contain bypassing verification checks and authentication mechanisms. A crucial weak spot might be a flaw within the FRP’s communication protocol, permitting an attacker to intercept or forge authentication requests.
Potential Hurt, Rom frp bypass
Exploiting these vulnerabilities can result in vital hurt. Probably the most rapid impression is the lack of possession and management of the gadget. Unauthorized entry permits an attacker to probably acquire entry to delicate private information saved on the gadget. This information can embrace pictures, movies, monetary data, and personal communications. The compromise of a consumer’s account related to the gadget may also result in the theft of different on-line accounts and providers.
So, you are making an attempt to bypass FRP in your ROM? Realizing how completely different calendars just like the Julian and Gregorian ( julian vs gregorian calendar ) have developed over time may not appear instantly associated, however understanding these historic modifications in timekeeping can generally provide help to recognize the intricacies of those bypass strategies. Finally, you may nonetheless want the suitable instruments and strategies to get the job finished!
Moreover, the gadget may be used for malicious actions, similar to sending spam or collaborating in cyberattacks.
Illustrative Exploitation Flowchart
The next flowchart illustrates a simplified means of exploiting a hypothetical vulnerability within the FRP system’s authentication mechanism. Be aware that it is a simplified illustration, and precise bypass strategies may be much more advanced.
| Step | Motion |
|---|---|
| 1 | Determine a vulnerability within the FRP authentication protocol. This vulnerability may contain a weak encryption algorithm or a buffer overflow. |
| 2 | Develop an exploit code to leverage the recognized vulnerability. This code may contain crafting particular requests to the system or manipulating reminiscence addresses. |
| 3 | Deploy the exploit code to the goal gadget. This might be achieved by way of numerous means, similar to putting in a modified ROM or injecting malicious code. |
| 4 | Execute the exploit code. The code will try and bypass the authentication mechanism. |
| 5 | If profitable, the attacker positive factors entry to the gadget. |
Stopping ROM FRP Bypass
FRP bypass exploits vulnerabilities in Android’s preliminary setup course of, making gadgets susceptible to unauthorized entry. Producers want sturdy methods to safe their gadgets towards these assaults. This part particulars proactive measures to strengthen Android gadgets towards FRP bypass makes an attempt.
Strengthening System Safety
Producers can implement a number of layers of safety to mitigate the chance of FRP bypass. These methods ought to concentrate on making the preliminary setup course of extra immune to exploitation.
Superior Authentication Mechanisms
Including multi-factor authentication (MFA) throughout preliminary setup can considerably enhance safety. This may contain requiring a second type of verification, like a one-time code despatched to a registered cellphone quantity or electronic mail deal with. Biometric authentication, similar to fingerprint or facial recognition, can be used along side passwords to create a safer login course of. Implementing sturdy password insurance policies with advanced necessities may also deter brute-force assaults.
Enhanced Bootloader Safety
Safe bootloaders are essential in stopping unauthorized modifications to the Android system. Utilizing safe bootloaders ensures that solely trusted software program is loaded in the course of the boot course of, hindering attackers from putting in malicious software program or bypassing safety measures. This may be achieved by implementing safe boot protocols and making certain the integrity of the bootloader firmware.
Safe Storage and Information Encryption
Defending delicate information saved on the gadget is significant. Finish-to-end encryption of crucial information and storage partitions can forestall unauthorized entry even when the gadget is compromised. Implementing sturdy encryption algorithms and protocols can additional safeguard information confidentiality.
Common Safety Updates and Patching
Producers ought to promptly launch and deploy safety updates that deal with identified vulnerabilities. This contains patching any flaws that might be exploited by FRP bypass instruments. A proactive strategy to safety updates ensures that gadgets are protected against rising threats.
Desk of Preventative Measures
| Preventive Measure | Effectiveness | Implementation Price |
|---|---|---|
| Multi-factor authentication (MFA) throughout preliminary setup | Excessive – Provides a major layer of safety | Medium – Requires growth and integration effort |
| Safe Bootloader | Excessive – Prevents unauthorized modifications | Excessive – Requires safe boot implementation and verification |
| Finish-to-end encryption of delicate information | Excessive – Protects information even when gadget is compromised | Medium – Requires encryption implementation and upkeep |
| Common safety updates and patching | Medium – Addresses identified vulnerabilities | Low – A part of common software program upkeep |
| Robust password insurance policies | Medium – Makes brute-force assaults tougher | Low – Coverage implementation is comparatively easy |
Influence on System Producers
ROM FRP bypasses, whereas providing comfort to customers, pose vital challenges for gadget producers. The convenience of bypassing manufacturing unit reset safety can severely impression their backside line and model status. Producers should constantly adapt to those evolving safety threats.Producers face a fancy net of points, from sustaining their status to coping with the monetary repercussions of widespread bypasses.
This contains the price of growing and implementing stronger safety measures, and the potential lack of income resulting from decreased gross sales or elevated restore prices.
Monetary Implications
The price of growing and implementing sturdy safety measures, together with stronger FRP safety, is a major monetary burden. This usually contains devoted analysis and growth groups, up to date software program, and potential {hardware} modifications. Producers have to weigh the price of these safety enhancements towards the potential monetary losses from user-initiated bypasses. For instance, if numerous gadgets are reported with bypass points, restore prices for these gadgets might improve, which is able to scale back the general revenue margin.
As well as, there may be authorized liabilities related to vulnerabilities within the FRP system.
Operational Implications
FRP bypasses can create operational challenges for producers. The rise in unauthorized entry to gadgets results in a better demand for buyer help, troubleshooting, and probably escalating disputes with customers. Producers should additionally think about the potential impression on their restore processes. If numerous gadgets are being bypassed, restore facilities might face an inflow of gadgets with related points, requiring specialised troubleshooting.
Influence on Model Fame
System producers rely closely on their model status for buyer belief and future gross sales. When FRP bypasses change into widespread, the model picture can endure a major blow. Customers might understand the gadget as much less safe, which might result in a lower in gross sales and potential destructive publicity. This impression is very noticeable within the high-end market, the place safety is paramount.
For example, if a flagship cellphone mannequin repeatedly suffers FRP bypass vulnerabilities, it might result in decreased market share and a diminished notion of high quality. The status loss may also result in long-term gross sales decreases as clients might select competing manufacturers.
Safety Enhancement Methods
Producers are using a wide range of methods to mitigate the impression of ROM FRP bypasses. These methods usually contain a multi-faceted strategy that features:
- Strengthening safety protocols: This contains steady enchancment of the FRP system’s algorithms, implementation of multi-layered safety checks, and incorporating hardware-based safety measures. This strategy goals to make bypasses tougher and time-consuming.
- Creating proactive safety updates: Producers continuously launch safety patches to deal with vulnerabilities of their working techniques. This proactive strategy goals to shut safety loopholes earlier than they are often exploited.
- Enhancing consumer schooling: Producers usually present assets and knowledge to customers on methods to preserve the safety of their gadgets and the significance of avoiding unauthorized software program. This will help scale back the variety of incidents attributable to consumer error.
- Collaborating with safety researchers: Collaborating with unbiased safety researchers to establish and deal with vulnerabilities is an important part. This helps producers keep forward of the curve within the ongoing safety battle.
Authorized Issues
The authorized panorama surrounding ROM FRP bypasses is advanced and varies by area. Producers want to concentrate on potential authorized liabilities associated to safety vulnerabilities of their merchandise and the ensuing harm or inconvenience to customers. This could contain mental property rights, information privateness, and shopper safety legal guidelines.
Technical Particulars of ROMs and Bypasses
ROMs, or customized working techniques, are modified variations of Android or different cell OSs. These modifications can vary from aesthetic tweaks to vital efficiency enhancements or safety modifications. They seem to be a highly effective device for customers desirous to personalize their gadgets, but additionally introduce complexity for these making an attempt to bypass Manufacturing facility Reset Safety (FRP). Understanding how ROMs work is essential for comprehending the vulnerabilities they will introduce and the way bypasses exploit them.The technical particulars of ROMs and FRP bypasses are intricately linked.
Bypasses usually goal particular parts inside a ROM to use weaknesses, and a deeper understanding of those parts is significant for stopping such assaults. ROMs aren’t simply beauty modifications; they alter the basic construction and functionalities of the working system. Because of this bypassing FRP in a customized ROM usually requires specialised strategies tailored to the actual ROM’s structure.
Completely different ROM Sorts and Functionalities
Customized ROMs are available in all kinds of flavors, every with its personal strengths and weaknesses. Some well-liked sorts embrace LineageOS, Pixel Expertise, and AOSP-based ROMs. These usually supply enhanced efficiency, privateness controls, and prolonged software program help. Different ROMs might concentrate on aesthetics or particular {hardware} options. Every ROM has its distinctive strategy to core system modifications.
Technical Particulars Behind Bypass Strategies
Bypass strategies range significantly relying on the particular ROM and the focused vulnerability. Some exploit vulnerabilities within the system’s authentication processes, whereas others concentrate on bypassing safety checks throughout the working system kernel. Understanding the particular structure of the focused ROM is essential for tailoring the bypass method.
Construction of a Typical ROM and Focused Areas for Bypass
A typical ROM construction contains a number of key parts. The kernel, the core of the OS, is essential. The system libraries present core functionalities, and the applying framework facilitates the interplay between apps and the OS. The focused areas for bypass usually contain:
- Kernel-level vulnerabilities: Exploiting bugs within the kernel, the bottom stage of the OS, can grant unauthorized entry. That is usually probably the most advanced and probably harmful strategy.
- System library manipulation: Modifying or changing system libraries can enable bypassing safety checks with out instantly interacting with the kernel. This may be achieved by injecting malicious code or altering current functionalities.
- Software framework interception: Interfering with the way in which purposes work together with the OS can alter how authentication checks are carried out. Refined bypasses may exploit weaknesses within the interplay between apps and safety parts.
- Account administration: Bypassing FRP usually entails manipulating or circumventing account authentication procedures, which is an important space of focus for builders of bypass instruments.
By understanding these focused areas, builders can create bypasses which are tailor-made to particular ROMs. This customization is essential as a result of a bypass efficient on one ROM may not work on one other.
Interaction Between ROMs and Bypass Procedures
The interaction between ROMs and bypass procedures is essential for safety. A ROM’s modifications can create new vulnerabilities or masks current ones, making it tougher to defend towards FRP bypass makes an attempt. The selection of ROM can affect the effectiveness of safety measures. A security-focused ROM could have completely different safety implementations than a ROM centered on customization, resulting in assorted approaches to bypass makes an attempt.
Conclusion: Rom Frp Bypass
In conclusion, ROM FRP bypass presents a captivating however probably dangerous space of cell gadget safety. We have explored the various strategies, strategies, and issues surrounding this follow. Whereas bypassing FRP could be a great tool in particular circumstances, understanding the authorized, moral, and safety implications is paramount. Producers should constantly try to enhance safety measures, and customers must be conscious of the dangers related to using bypass strategies.
Detailed FAQs
What are some widespread strategies for ROM FRP bypass?
Numerous strategies exist, starting from exploiting particular vulnerabilities within the gadget firmware to utilizing specialised software program and instruments. Some contain bypassing the FRP lock display, whereas others might contain modifying the gadget’s working system (ROM).
What are the potential dangers of utilizing ROM FRP bypass strategies?
Using ROM FRP bypass strategies can result in authorized points, moral issues, and safety vulnerabilities. Unauthorized entry to gadgets can have penalties, and customers might face penalties relying on the jurisdiction and particular strategies used.
How can gadget producers strengthen their gadgets towards FRP bypass?
Producers can make use of sturdy safety protocols, often replace firmware, and implement multi-layered safety measures to mitigate the dangers related to FRP bypass.
